Learn how to completely remove Locky ransomware, how Locky ransomware attacks work, and how you can prevent Locky from infecting your computer. You can eliminate this ransomware in a few easy steps by following the instructions to remove viruses in this article, and you can also safeguard your Mac from potential dangers.
Contents: Part 1. Simple Clicks to Remove Locky from MacPart 2. What Is the Locky Virus?Part 3. Protect Your Mac from the Locky RansomwarePart 4. Conclusion
Part 1. Simple Clicks to Remove Locky from Mac
With iMyMac PowerMyMac, you can fix and enhance your Mac. It combines a wide variety of useful functionality with an excellent user interface. This Mac cleaning tool makes it simple to locate and remove redundant and linked files.
During the uninstall process, you just need to click a few times to do the job. Let's examine the details of the way it functions right now. To get rid of any leftovers and unnecessary software, use the PowerMyMac App Uninstaller utility. It gives a very useful technique for removing programs from a Mac.
You may easily remove Locky and all related files by using the fantastic App Uninstaller program. Finding every file required for a piece of software may take some time. Not only can you remove ransomware software easily, but you can also remove redirect viruses such as deleting Zeus virus completely from Mac.
Follow these steps to see whether this application is efficient in removing unneeded or undesirable applications:
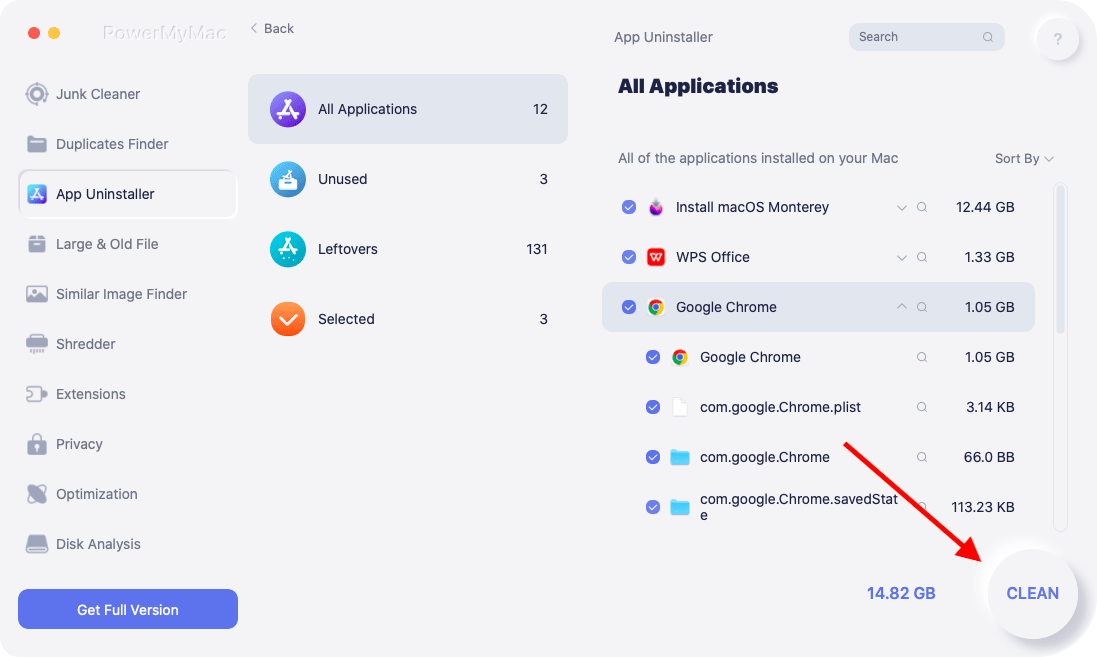
- Open PowerMyMac, then chooses Settings from the drop-down menu that opens. When the selection of options comes below, select App Uninstaller.
- After choosing a computer, click the SCAN button to begin a full examination of the software settings on that device.
- Every software that is now running on your device will be displayed and you'll be given the option to remove them. Additionally, you might try putting the program's name in the search bar to see if it helps.
- Any Locky-related data on your device will be deleted if you choose "CLEAN."
- When it's finished, the phrase "Cleaned Completed" ought to show up on the screen.
Part 2. What Is the Locky Virus?
One of the numerous ransomware samples that linger online is Locky. It encrypts the computer or device of the targeted victim before demanding a ransom from owners in return for a code that would unlock the encryption for your PC.
Initially, malware gets onto your computer via shady emails that might fool you into installing an app or piece of software through a link connected to it. Your consent will be required in order for the harmful software that fraudsters have built to operate.
Next, it locks your screen or just encrypts your data to prevent you from accessing them. A message requesting a particular amount be sent to a certain account or method that the hacker prepared will appear on your screen.

The letter would promise to offer you the Locky ransomware decryptor key, which would be used to disengage the lock and restore your access to its proper owner. The malicious attachment in the fake email that targets receive allows Locky to infect their PC.
With subject lines like "Upcoming Payment - 1 Month Notice," these emails often seem to be paid invoices. Nobody loves owing money. Thus, the victims are motivated to read the emails by this sentiment. Another option is to safeguard your Mac against Locky Ransomware to avoid any problems or the need to remove Locky.
Part 3. Protect Your Mac from the Locky Ransomware
Ransomware is among the most challenging forms of malware to handle after you've been infected. The greatest defense tactic is always prevention for you to save problems and the need to remove Locky. To protect your computer against Locky and other ransomware, be attentive and adhere to some basic precautions:
- Any dubious attachments or URLs should not be opened. Before opening a document, make sure you are familiar with and confident in its source. Cybercriminals that like sending emails to you rely upon you to acquire or download their attachments. Stay away from their traps.
- In Office for Mac, disable all macros by default, and never turn them on in any shady documents you get. When you turn on macros in the Word document supplied, Locky's installation method begins to work. Go to Preferences > Security & Privacy in Word, Excel, or PowerPoint while they are open, then choose the required settings.
- Back up your data often to the cloud or an external disk. Back up your data sometimes, whether you're utilizing an external drive or a cloud service. When your backup is finished, if you choose to use a removable storage device, detach it immediately.
- As soon as updates and fixes are available, install them on your computer. Numerous malware assaults depend on flaws in obsolete software's security.
- Establish a routine for checking your Mac for viruses. Not only will a reliable cybersecurity solution protect you against ransomware but also from other malware and hacking attempts.

Part 4. Conclusion
Now you have learned the best method to remove Locky ransomware from your machine. All of the key ransomware features, including massive spam email campaigns, a BTC payment method, and many programming languages, are run by Locky.
Fortunately, keeping your Mac safe and clean from this and other malware is not too difficult. Simply take the recommended simple safety measures to safeguard your Mac. You may be confident to remove Locky from Mac is straightforward with just a few clicks if you use PowerMyMac.



